It’s tremendously unfortunate that while the world hunkers down to ease the escalation of COVID-19, hackers are taking advantage of the chaos and capitalizing on our need for information. In our haste to learn more, it is easy to forget to check before we click, and that is exactly what every hacker wants. Cybercriminals use the latest hot media topic to their own benefit.
Hackers often disguise their identity to appear as someone we know and use links that appear credible. This is known as social engineering. Here are a few things to keep your eyes open for:
Fake Tracking Maps:
There are a number of COVID-19 dashboards available on the internet, most notably the one published and updated by John Hopkins University, that includes helpful statistics like outbreak areas and the amount of people infected there. Internet users should beware, however, of a malicious map embedded with malware circulating through infected email attachments and online advertisements. This map looks exactly like John Hopkins University’s map but contains spyware that tracks passwords and credit card numbers stored in your browser. Similarly, a text message is going around that sends a link to download an application disguised as the actual Corona Live application from John Hopkins University. Once installed, a customized version of SpyMax, an Android remote administration tool, can allow hackers access to your smartphone camera, listen through your microphone, and access your text messages.
Be wary of emails sharing COVID-19 maps, and do not install them on your Windows system. Stick with the official, safe dashboards. The legitimate John Hopkins COVID-19 Dashboard is available here:
Emails from WHO, CDC, FDA, or EPA
There are a multitude of scammers pretending to be representatives from government organizations like the World Health Organization (WHO) and the Centers for Disease Control and Prevention (CDC). Cybercriminals design emails, text messages, and even websites to look like official communication to trick users to click malicious links or download infected attachments.
Here is an example:
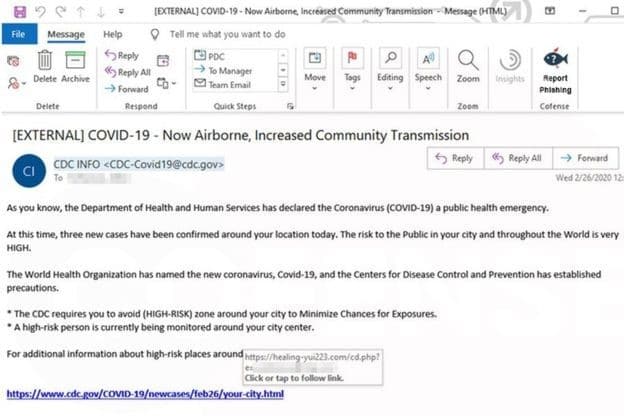
Even though this email looks valid, you can see that when this embedded hyperlink was hovered over, the URL does not match the anchor text. If the email recipient is not extremely careful, they may not notice the trap until it is too late. This is also tricky when viewing emails from your handheld device, as it is more difficult to hover a cursor over a link without clicking it if you are not using a mouse.
It’s also important to note that while most malicious attachments are .zip files, any attachment file type can contain a virus. This is why it is extremely important that you only open attachments from people you know and trust.
Here is another example:
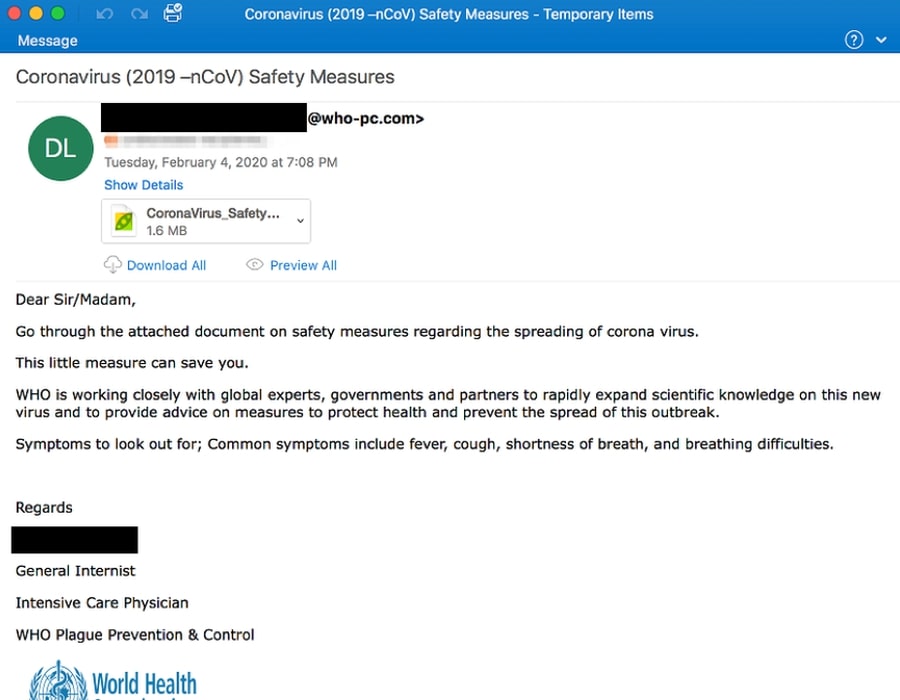
While this email also appears to be authentic, notice that the email address is from @who-pc.com. WHO emails are addressed @who.int. WHO does not send email from addresses ending in @who.com, @who.org or @who-safety.org. Emails from the CDC are addressed @cdc.gov.
Emails or Texts from Your Boss or HR
During this time, we are seeing an increase of cybercriminals targeting small businesses by posing as a company official and either asking for personal information (ie: fill out this form) or instructing the recipient to click on something. Like this one:
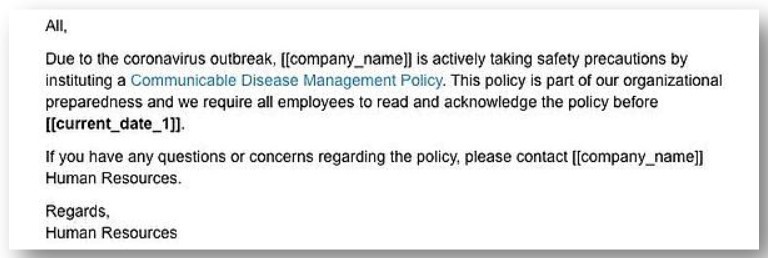
These are very sneaky because if you email with this person regularly, you may not hesitate to complete their request. This could also happen over text message. Phishing campaigns carried out over text message are known as smishing, and are becoming more common. The first clue you should look out for is that Human Resources already has your information and should not be asking you to respond with personal information over email or text. When in doubt, pick up the phone, call the assumed sender, and verify that everything is on the up and up. In general, you should hover your cursor over any link that is emailed or messaged to you before clicking on it.
What to Look Out For
Keep your eyes peeled for spelling and grammatical mistakes, generic greetings, requests for personal information, and emails that sound urgent. These are red flags for a phishing email.
What You Can Do
- If you are unsure, contact your company’s IT technician and ask for help before you click on a link or open an attachment.
- It’s important to keep your operating system up to date. You can go to the Window settings and click on Updates and Security. From there, you can click on updates to make sure your computer is up to date.
- Use an antivirus. Check with your IT Department and make sure you have the latest security protection software updates installed on your office and home computer. Enable real-time scanning, so that if you accidentally click or download the wrong thing, real-time scanning will catch it and prevent your system from being damaged.
- Change your cell phone settings to update software automatically.
- Do not root (Android) or jailbreak (Apple) your mobile devices. This means removing or bypassing default security protections that were built into the operating system. Some people do this to gain escalated privileges that allow them to take actions that they otherwise would be unable to as they are prohibited by the operating system, but this compromises the built-it security features of the device.
- Use multi-factor authentication whenever possible. This prevents hackers from using stolen passwords to log into accounts. In this same line of thought, you should use unique strong passwords for each account.
- Backup your data regularly and have a backup offline.
- Do not open attachments or click links, either from your cell phone or computer, if you do not recognize the sender of the email. Even check on email addresses and links of known senders before clicking on anything.
- Do not give out your private information including username, password, date of birth, social security number, or financial data in response to an email, social media message, text, or robocall.
- If someone asks you to call a number provided in an email, look up the phone number on the company’s website to verify it before calling.
COVID-19 is changing the way all of us operate. Check out this article on how to work from home productively. If your business is in need of solutions to work remotely, please contact us for more information.






